Safeguarding Your Privacy in a Smart Home: The Ultimate Guide
Smart Homes and Protecting Your Privacy
If you’re a first-time homebuyer, you may be excited to explore the world of smart homes. These technologies—ranging from voice-activated assistants to automated lighting and thermostats—provide convenience and comfort but also carry privacy risks.
According to recent surveys, over 70% of homebuyers now express interest in installing the best smart home security systems 2025 has to offer. However, a study by the Internet Security Alliance found that 60% of smart home device users are unaware of potential threats and haven’t learned how to secure your smart home devices effectively. Because smart gadgets connect to the internet, your personal information can become vulnerable to hackers, with some reports indicating that over 30% of households experienced a cyberattack in the past year.
In this article, you’ll discover top smart home security tips and tricks, including how to prevent hacking in smart home devices, how to avoid smart home security mistakes, and why smart home security is important. You’ll also learn about affordable DIY smart home security solutions to protect your data and privacy in smart homes.
Understanding Smart Home Privacy Risks
Modern smart homes are brimming with connected devices that track details about your daily routine—everything from energy usage patterns to voice commands. This constant data flow can expose you to various vulnerabilities if you don’t take measures to protect it.
What Are the Risks?
- Data Collection: Devices often gather personal information about your habits and preferences, raising concerns about invasion of privacy.
- Unauthorized Access: Weak networks or default passwords can open the door to cybercriminals.
- Third-Party Sharing: Some companies might sell your data to marketers or share it with partners.
- Location Tracking: Products like smart home security cameras with privacy features can still reveal your routine if intercepted.
Why smart home security is important: By understanding these potential dangers, you’ll better appreciate how to secure your smart home devices and keep your personal data safe.
The Rising Popularity of Smart Homes
Smart homes are becoming a big part of our lives, raising important privacy and security considerations.. Voice-activated devices, automated lighting, and internet-connected appliances promise unprecedented convenience. Yet, this convenient lifestyle often relies on constant connectivity, creating more opportunities for malicious actors to interfere. Protecting smart homes from cyberattacks starts with recognizing these risks and applying the right security practices.
Secure Network Configuration

One of the top concerns for smart homeowners is network safety. A properly configured network is your first barrier against unwanted intrusions.
- Use Strong Credentials to safeguard your smart home network from unauthorized access.: Choose a robust password for your Wi-Fi and change the default router login.
- Enable Encryption: WPA2 or WPA3 encryption helps block unauthorized users.
- VLANs & Guest Networks: Creating a separate network or using a VLAN specifically for smart home devices can limit access to your primary network.
- Firewalls & Intrusion Detection are essential for maintaining security in smart home IoT environments. Installing additional security layers is among the best practices for smart home cybersecurity, especially for smart thermostats.
Following these steps is crucial for how to prevent hacking in smart home devices and reduce the odds of external threats.
Firewalls: Your Smart Home’s First Line of Defense
As your smart home grows more connected, securing it becomes essential, and nothing protects your home network better than a firewall. Acting as a digital gatekeeper, firewalls monitor incoming and outgoing traffic to keep malicious threats out while allowing legitimate activity through. Whether it’s ensuring your smart doorbell only communicates with its server or blocking suspicious attempts to hack your smart thermostat, firewalls provide an essential layer of protection for your connected devices.
What Does a Firewall Do?
Firewalls are designed to protect your home network from unauthorized access and cyber threats. They build a virtual shield around your devices, scanning data packets that enter or leave your network. If the firewall detects anything suspicious—like viruses, malware, or harmful unauthorized access attempts—it automatically blocks it.
Firewalls can operate on multiple levels:
- Packet Filtering: Examining small data packets based on pre-defined criteria to allow or deny their passage.
- Network Address Translation (NAT): Allowing devices to share a single public internet connection while hiding the internal network from outsiders.
- Stateful Inspection: Monitoring traffic patterns in real-time and detecting unusual or dangerous activity.
How Are Firewalls Implemented?
Firewalls can be implemented as:
- Software Firewalls: Installed directly on devices like laptops, PCs, or even smartphones. These tend to work best for securing individual machines.
- Hardware Firewalls: Stand-alone, dedicated devices that protect the entire home network, creating a barrier at the router level. These are often more effective in homes with multiple IoT (Internet of Things) devices.
Benefits of Using a Firewall in a Home Network Environment
A firewall shields your home network in several significant ways:
- Protecting IoT Devices: Connected devices like smart cameras, thermostats, or light bulbs often have weaker security measures. A firewall ensures these endpoints are safe from malicious actions.
- Blocking Malware: It prevents viruses, ransomware, and phishing attacks before they can infect your devices.
- Intrusion Detection and Prevention: Firewalls monitor network activity for breaches and stop unauthorized access attempts.
- Ad Blocking and Content Filtering: Many firewalls allow you to block intrusive ads and filter out harmful or inappropriate content, providing safer browsing for your household.
- Parental Control Features: Some firewalls come with tools to monitor and manage internet usage for children, ensuring a safer online experience.
- VPN Integration: Many firewalls support Virtual Private Networks (VPNs), making it easy to secure remote connections and shield your online activity from prying eyes.
A Popular Solution: Firewalla
If you’re looking for a simple, affordable, and robust hardware firewall, the Firewalla is an excellent choice. This compact device offers enterprise-level security for both home and business use. Here are some of its key features:
- Comprehensive Cybersecurity: Firewalla detects and blocks malware, hackers, and suspicious activity automatically.
- Smart Parental Control: Manage and monitor your kids’ online activity to ensure safe browsing habits.
- Ad Blocking: It can filter out online ads for a cleaner internet experience.
- VPN Server and Client: Use it to establish encrypted connections both within and outside your home, perfect for ensuring secure remote work.
- No Monthly Fee: Unlike many subscription-based services, Firewalla provides all these features without ongoing costs.
Setting up Firewalla is simple: connect it to your home router, install the companion app, and configure it according to your preferences. Whether you’re a tech novice or an expert, Firewalla’s intuitive interface makes securing your smart home easier than ever.
READ: Full Firewalla Product Review
Investing in a firewall like Firewalla is a wise choice. Not only does it provide robust security for your network, but it also enhances your family’s online experience by adding features like parental controls and ad blocking. With the rise of cyberattacks and the increasing dependence on IoT devices, a firewall isn’t just a luxury—it’s a necessity.
Firewalla: Cyber Security Firewall for Home & Business
Smart Device Management
Choose Reputable Brands
Select trusted manufacturers known for reliability and frequent firmware updates. Look for products that actively address smart home security vulnerabilities and how to fix them. You can also check a device’s privacy reputation through independent tests or certifications.
Disable Unneeded Features
Avoid enabling features you don’t use (e.g., location tracking or persistent listening modes). This helps minimize data collection and closes off potential entry points that attackers might exploit.
Use a Password Manager & VPN
A Virtual Private Network (VPN) encrypts traffic, which helps in protecting your data and privacy in smart homes. A Using a password manager can help secure your smart home IoT devices effectively. Using a password manager can safeguard unique passwords across devices in your smart home system.
Smart Home Security Cameras with Privacy Features
Modern cameras often include advanced encryption and data protection. When shopping for the best smart home security systems 2024, confirm the devices you consider have built-in privacy shutters, multi-factor authentication, or encryption for recorded footage.
Regular Software Updates
Manufacturers release updates to patch security holes and enhance performance. If your devices don’t update automatically, periodically check for new releases to ensure your smart home network remains secure. Regular updates not only protect software but also serve as a key component of how to avoid smart home security mistakes.
Setting Up a VLAN for Enhanced Home Security
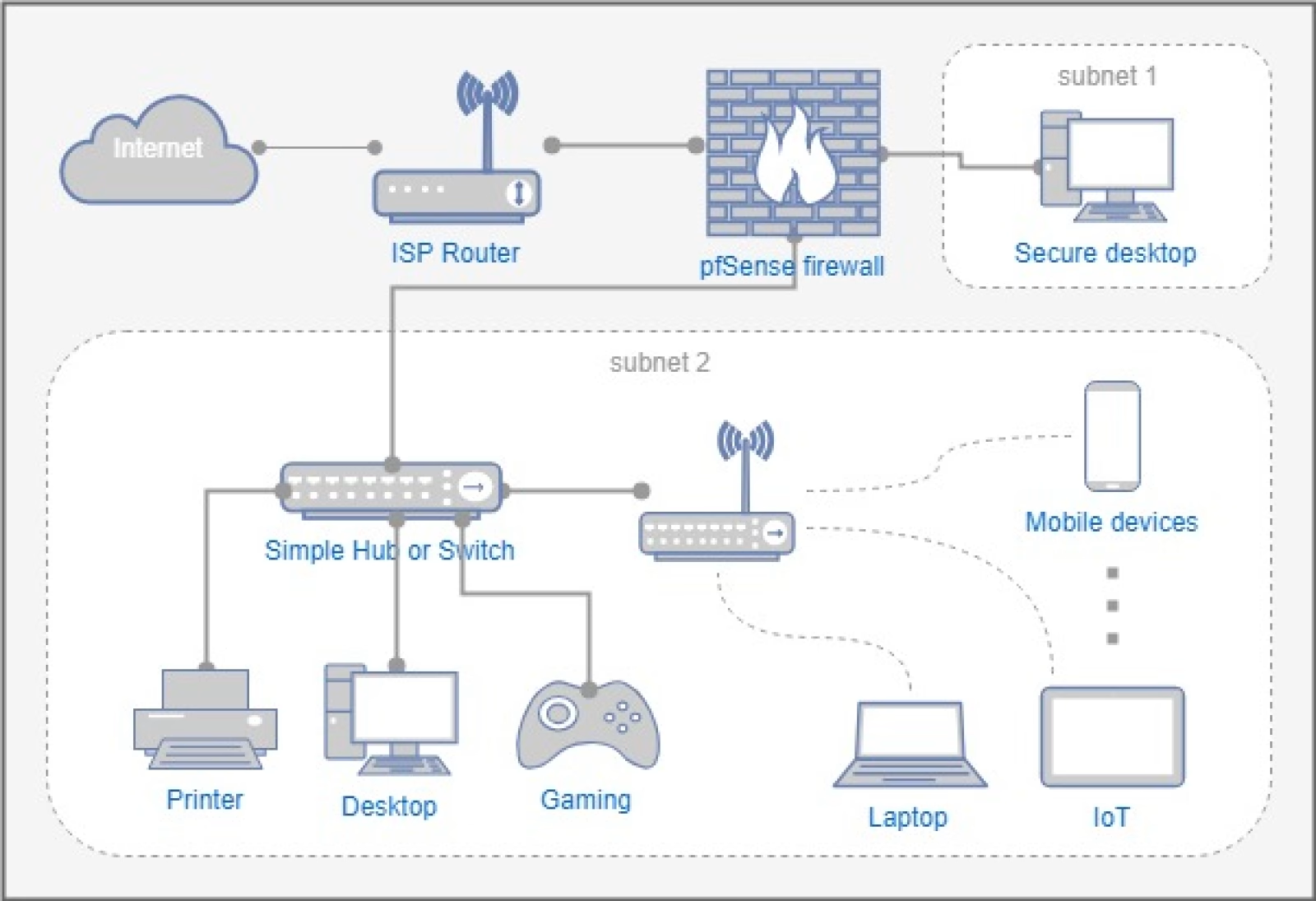
A Virtual Local Area Network, or VLAN, splits a single physical network into multiple compartments, allowing you to isolate devices based on their function—even if they share the same hardware. This setup is a powerful strategy for protecting smart homes from cyberattacks.
- Separate IoT Devices: Group your smart speakers, cameras, and thermostats on one VLAN.
- Keep Personal Data Separate: Place computers, phones, and other personal devices on another VLAN to enhance your home network security.
- Control Traffic Flow: Restrict the paths between VLANs, so that malicious actors face significant roadblocks.
By combining smart automation and home security measures, you add multiple layers of defense while keeping devices organized.
VLAN Requirements
You can certainly add a VLAN to an existing setup. All it takes is a router or managed switch that supports VLAN configurations. Many modern routers already include this capability, so check your device’s documentation or user settings to confirm whether it’s VLAN-ready.
From there, you simply log in to the administrative console, assign a VLAN ID, and decide which ports or wireless connections belong in each VLAN. Although this might initially seem technical, most manufacturers provide straightforward setup guides.
Popular Routers Supporting VLANs
ASUS RT-AX88U
Manufactured by ASUS, the RT-AX88U is a popular Wi-Fi 6 router known for its straightforward VLAN configuration. One standout benefit is its adaptive Quality of Service (QoS), which optimizes bandwidth for high-priority tasks like gaming or streaming. This means you can comfortably segment your home network without compromising performance.
Netgear Nighthawk RAXE300
From Netgear’s esteemed Nighthawk lineup, the RAXE300 supports VLANs and delivers ultra-fast Wi-Fi 6 speeds. What sets it apart is the tri-band architecture, which handles more devices simultaneously while maintaining strong signal stability. If you have a busy smart home with multiple IoT gadgets, this router’s extra band can shoulder the load.
TP-Link Archer AX6000
Produced by TP-Link, the Archer AX6000 also enables VLAN segmentation and offers an extensive suite of security features, such as HomeCare antivirus and parental controls. Its advantage over many competitors lies in its powerful processor and eight high-speed Gigabit LAN ports, ensuring seamless wired and wireless connections even in larger households.
Zero-Trust Network Approach
Even if you segment your network with VLANs, it helps to imagine every device as potentially compromised until proven otherwise. This “zero-trust” mindset encourages you to verify and validate each gadget’s security posture whenever it accesses your network. You accomplish this by keeping firmware up to date, restricting permissions to only what’s absolutely necessary, and routinely scanning for any signs of unusual activity. By treating even your most trusted smart thermostats or lighting systems with caution, you reduce the chance of overlooking vulnerabilities that could give hackers a foothold in your home.
- Zero-trust means setting strict rules for how devices communicate.
- For example, your voice assistant shouldn’t send data to your security cameras without permission.
- This approach ensures all cross-network communication is authorized.
- It helps protect private information, like video footage and voice commands, from unauthorized access.
Detailed Device-Specific Privacy Settings
Major platforms like Alexa, Google Home, and Apple HomeKit offer more privacy controls than many people realize. You can review and disable voice recordings, limit how often your device learns from your interactions, or prevent your system from storing transcripts indefinitely. In the Alexa app, for instance, you can delete individual voice commands or purge them in bulk whenever you want. Meanwhile, Google Home allows you to pause or turn off certain types of data collection related to personalized recommendations, and Apple HomeKit restricts device data access through end‑to‑end encryption. [READ MORE]
- Take a few minutes to adjust hidden settings to better protect your household’s privacy.
- Turn off location tracking for unused features.
- Disable devices from storing unnecessary usage logs.
- These small changes give you more control over what data is shared outside your home.
- Enjoy peace of mind knowing your personal information is protected and tailored to your comfort level.
Physical Security Aspects
Even the strictest network defenses won’t help if a malicious actor can simply slide your router out of its place or walk away with an unsecured smart device. Locking up your networking equipment—or placing it in a spot that only you and trusted family members can reach—helps prevent tampering.
- If a thief physically accesses your camera or voice assistant, they could extract data or reset it to factory settings, bypassing your security.
- Always use encryption and password protection on all devices.
- A stolen device without a passcode can expose sensitive information like video footage or user preferences.
- Combine physical security measures with strong digital defenses to better protect your network from potential attacks.
Understanding Why Smart Home Security Is Important
Taking the time to plan proper security measures protects you from data breaches and helps maintain your peace of mind. By knowing how to secure your smart home devices, you’ll also gain insights on privacy protection strategies.
- How to prevent hacking in smart home devices and protect against potential privacy invasions.
- Affordable DIY smart home security solutions
- Securing smart locks and IoT devices in your home
When you implement robust security steps and stay vigilant, you minimize vulnerabilities in your home environment that could otherwise compromise your personal information.
Evaluating Smart Home Products
Privacy Policies Review
Before purchasing any new gadgets, examine privacy policies closely. Look for details on encryption, data-sharing practices, and whether the company addresses privacy concerns by selling your data to third parties.
Manufacturer Reputation
Opt for well-known brands with consistent security protections and transparent policies on software updates to ensure your smart home system is secure. Below is a sampling of trusted brands known for focusing on best practices for smart home cybersecurity and addressing privacy issues.
| Company | Security Practice |
| Apple | Known for its strong emphasis on privacy and security in its smart home products. Integrates robust encryption, including HomeKit’s secure ecosystem. |
| Google Nest | Employs regular security updates and multi-factor authentication to protect against potential privacy issues in smart home networks. |
| Eero | Updates firmware frequently and uses WPA3 encryption |
| Ubiquiti | Offers enterprise-grade security features in UniFi product lines |
| Netgear | Implements password strength requirements and frequent firmware updates |
| Synology | Provides built-in VPN support and comprehensive security audits |
| Arlo | Emphasizes end-to-end encryption for video streams |
| Logitech | Maintains data encryption and invests in regular firmware security to protect smart home users from potential privacy risks. |
| Philips Hue | Regularly updates its smart lighting hubs and encourages secure connections via strong encryption. |
| Ecobee | Focuses on secure data transmission through encryption and enforces strict privacy controls in its thermostat offerings. |
Google Home and Alexa Security Tips for Smart Homes
Voice assistants may collect, store, and analyze voice commands. If you’re using Google Home or Alexa devices, here are a few ways to make sure you’re protecting your data and privacy implications in smart homes:
- Review Voice Recordings: Regularly delete or manage stored queries.
- Set Up PINs or Voice Codes to enhance privacy protection in your smart home environment.: Lock down sensitive tasks (e.g., purchases) with passcodes.
- Optimize App Permissions to limit the data collected by your smart home devices.: Limit the amount of personal data your apps can access.
Setting Clear Boundaries
Define which data you are comfortable sharing and what should remain private. For example, you may allow your device to track energy usage but prefer to keep personal details (like name and address) off-limits. Review each device’s privacy policy to see how data is collected, used, and shared. This helps you make informed decisions and retain control over your information.
Creating User Profiles
Establish user profiles that let you dictate what data each person can access and what tasks they can perform. For instance, you might restrict your children’s access to certain devices or features, while giving other adults more extensive control. Review these profiles regularly to ensure they stay in line with your privacy expectations.
By disabling unnecessary voice recordings, limiting data collection, and anonymizing usage statistics, you can strengthen the confidentiality of your smart home.
DISABLING VOICE RECORDINGS IN SMART SPEAKERS
Amazon Alexa
- Manage Voice Recordings
- Open the Alexa app and go to “Settings.”
- Under “Alexa Privacy,” select “Review Voice History” to delete stored recordings.
- Opt out of human review by disabling the relevant setting (often labeled as “Help Improve Amazon Services and Develop New Features”).
- Prevent Unauthorized Access
- Create a voice PIN or password for sensitive actions such as shopping or accessing personal information.
- Consider turning off “Personalized Results” in public spaces to limit data exposure.
Google Home
- Adjust Activity Controls
- Go to your Google Account’s “Data & Personalization” section.
- Disable or pause “Web & App Activity” and “Voice & Audio Activity” to limit data logging.
- Delete Voice Recordings
- Visit “My Activity” in your Google Account to review and delete audio clips or transcripts associated with Google Assistant.
- Use auto-delete schedules so data older than a certain period (e.g., three or six months) is automatically removed.
- Restrict Sharing
- Under “Home App” settings, check each device’s permissions and remove unnecessary or third-party app integrations.
Apple HomeKit
- Turn Off Audio Storage
- Access HomeKit settings within the Home app on your iPhone or iPad.
- For HomePod or HomeKit-enabled devices, disable “Allow Siri to use your voice input” when you don’t need constant listening.
- Limit Data Syncing
- Make sure you’re signed in with your Apple ID that has two-factor authentication enabled.
- Disable “Home” data syncing with iCloud if you prefer local-only control (found in “iCloud” settings on your iOS device).
- Check App Permissions
- Under “Privacy” settings, review what apps have access to HomeKit.
- Revoke or limit permissions for any apps that don’t require full control of your devices.
Smart Home Data Privacy & Security
Many smart devices share data with third parties, sometimes exposing personal information to additional risks. Companies may collect data for marketing or sell it to other entities. These concerns highlight why monitoring device settings and proactively choosing secure platforms are vital: they help mitigate smart home security vulnerabilities and how to fix them—before they become problems.
Data Retention and Local Storage Options
It’s not just about what your devices collect; how and where they store information can also shape your overall security. When you know the ins and outs of data retention, you’ll be better equipped to decide which smart home products to trust.
How Long Is Your Data Kept?
Many smart home manufacturers keep daily logs of activity—like motion sensor triggers or energy usage—for varying lengths of time. While some companies automatically delete old records after a set period, others might store them indefinitely. Make sure to check whether you can control how long the data remains on the company’s servers.
Local vs. Cloud Storage
Some devices offer local storage, meaning you can save video footage or logs on a memory card or personal server rather than relying on cloud services. This option limits how often your information travels across the internet, which lowers the risk of data leakage. Cloud-based systems are often easier to use and update remotely, but it’s essential to trust the provider’s security setup.
Third-Party Integrations
Even if you’re confident about a main device’s safety, supporting apps or connected services may have separate terms of use. For instance, voice assistants often link with other platforms to streamline tasks—everything from ridesharing apps to online shopping. Each partnership represents an additional data flow that can become a vulnerability. Before syncing multiple services, double-check privacy policies to confirm who accesses your personal information and why.
Minimizing Long-Term Exposure
Be cautious about features that store or display data histories, like daily routines or voice transcripts. Regularly clearing chat logs or removing unused Alexa skills can minimize your digital footprint. If you ever stop using a particular smart device, take time to factory-reset it and delete any lingering accounts that might still hold personal details.
Common Pitfalls & How to Avoid Smart Home Security Mistakes

- Default Credentials: Failing to change default usernames and passwords can leave you wide open to breaches.
- Ignoring Firmware Updates: Outdated software is an easy target for hackers.
- Overlooking network segmentation can lead to significant privacy issues in your home network.: Not creating guest networks or VLANs can expose your entire system.
- Allowing Excess Permissions: Granting apps or devices unnecessary privileges raises privacy risks.
Affordable DIY Smart Home Security Solutions
If high-end solutions aren’t in your budget, you can still take advantage of top smart home security tips and tricks on a shoestring:
- DIY Alarm Systems: Inexpensive door and window sensors can alert you to breaches.
- Used or Refurbished Cameras: Buying secondhand can save money, provided you update firmware immediately to protect your home IoT devices.
- Managed Services for smart home users can enhance the security of their devices.: Choose subscription-based models for crucial services like storage and advanced threat detection.
Final Nerdy Thoughts
Smart home technology offers comfort and convenience, but also inherent privacy challenges. By following the strategies above—securing your network, updating devices, learning how to secure your smart home devices, and practicing best smart home cybersecurity—you can enjoy the benefits while minimizing risks. Whether you’re researching the best smart home security systems 2024 has to offer or planning to implement affordable DIY smart home security solutions, a little diligence goes a long way in protecting your household.
Combining smart automation and home security ensures you make the most of innovative technology without compromising your personal data. Stay informed, stay updated, and take proactive steps so that your smart home environment remains functional and secure for years to come.
FREQUENTLY ASKED QUESTIONS
How can individuals enhance the security of their smart home devices?
To enhance the security of your smart home devices, start by choosing reputable brands that offer regular software updates and security patches. You should also ensure that your home network is secure by using strong passwords and changing them regularly. You should disable any unnecessary features on your smart home devices and only enable them when needed. It’s also important to monitor your devices and be aware of any unusual activity or changes in behavior.
What steps should we take to prevent unauthorized access to smart home systems?
To prevent unauthorized access to your smart home systems, start by securing your home network. This can be done by using a strong password and enabling two-factor authentication where possible. You should also disable any unnecessary features on your smart home devices and only enable them when needed. It’s also important to keep your devices up to date with the latest software updates and security patches.
In what ways can smart home technology impact personal privacy?
Smart home technology can impact personal privacy in a number of ways. For example, some devices may collect data on your behavior and preferences, which could be used for targeted advertising or sold to third parties. Some devices may be vulnerable to hacking or data breaches, which could result in sensitive information being exposed. It’s important to be aware of the privacy policies of your smart home devices and to protect your personal information.
What are the common vulnerabilities in smart home systems that could lead to privacy breaches?
Common vulnerabilities in smart home systems include weak passwords, unsecured home networks, and outdated software. Some devices may also have default settings that make them vulnerable to hacking. Some devices may collect data without the user’s knowledge or consent, which could be used for targeted advertising or sold to third parties. It’s important to be aware of these vulnerabilities and to take steps to protect your personal information.
Who is responsible for the data collected by smart home devices, and how can it be protected?
The responsibility for the data collected by smart home devices lies with the manufacturers and service providers. It’s important to read the privacy policies of your devices and to understand how your data is being used. To protect your personal information, choose reputable brands that offer regular software updates and security patches. You should also ensure that your home network is secure by using strong passwords and changing them regularly.
What are the best practices for maintaining privacy when using smart home technologies?
Keep your smart home secure by protecting your network, using reliable brands, and updating your devices’ software. You should also disable any unnecessary features on your devices and only enable them when needed. Additionally, you should be aware of the privacy policies of your devices and take steps to protect your personal information. Finally, it’s important to monitor your devices for any unusual activity or changes in behavior.
David Lawson is a veteran editor passionate about technology and storytelling. Armed with a journalism degree from Northwestern University, he crafts captivating narratives that demystify complex tech topics. With a knack for adapting to various styles, David collaborates on tech blogs, whitepapers, and best-selling books, helping innovators share their visions. Beyond writing, he explores smart home gadgets, attends tech events, and advocates for the transformative power of technology.











