Essential Guide to Firewalls for Home Networks and Small Offices

These days, our homes are packed with smart gadgets, and we’re pretty much always online. That’s why keeping your home network safe is so important. One of the best ways to do that? A hardware firewall. It’s like having a digital bodyguard for your devices—it keeps your personal info private and your family safe from cyber threats.
Here’s how it works: a firewall acts as a gatekeeper for your internet connection, deciding what gets in and what stays out. There are two kinds—hardware and software. Hardware firewalls are physical devices that protect your whole network, while software firewalls work on specific devices like your laptop or phone.
The great thing about a hardware firewall is that it covers everything on your network without needing to install anything on each device. From smart TVs to gaming consoles (even your smart thermostat and doorbell), everything stays protected. It blocks suspicious activity and keeps hackers, malware, and other bad stuff far away.
Plus, modern firewalls come with awesome extras like VPN support, parental controls, and intrusion detection systems. These features give you more control and extra peace of mind. Whether you’re streaming a show, working from home, or just browsing, a solid firewall has your back.
Key Takeaways
- Choose the Right Firewall: Not all hardware firewalls are created equal. Look for one that offers robust features such as intrusion detection and prevention, VPN support, and advanced filtering options. Popular brands include Cisco, Netgear, and Fortinet.
- Proper Configuration: Once you have your hardware firewall, it’s crucial to configure it correctly. Change the default admin username and password to something strong and unique. Disable any unnecessary services and ports to minimize potential entry points for attackers.
- Regular Updates: Keep your firewall’s firmware up to date. Manufacturers frequently release updates that patch vulnerabilities and improve performance. Enable automatic updates if available, or set a reminder to check for updates regularly.
- Network segmentation is crucial for enhancing the security of your computer or network.: Use your firewall to create separate network segments for different devices. For example, you can have one segment for your work devices, another for smart home gadgets, and a guest network for visitors. This limits the spread of malware and makes it harder for attackers to access sensitive information.
- Monitor Traffic: Regularly review the logs and alerts generated by your firewall. This can help detect unusual activity that could show a security breach. Some firewalls offer real-time monitoring and alerting features that can notify you immediately of potential threats.
- Enable VPN: If your firewall supports VPN (Virtual Private Network) functionality, use it to encrypt your internet traffic. This is especially important if you work from home or frequently access sensitive information online. A VPN can protect your data from being intercepted by cybercriminals.
- Educate Your Family: Ensure everyone in your household understands the importance of network security. Teach them about safe internet practices, such as recognizing phishing attempts and avoiding suspicious downloads.
- Backup Regularly: Even with the best security measures, breaches can still happen. Regularly back up important data to an external drive or cloud service. This ensures you can recover your information in case of a ransomware attack or other data loss incident. By implementing these steps, you can significantly enhance the security of your home network. A hardware firewall is a powerful tool, but it must be part of a comprehensive security strategy that includes regular updates, proper configuration, and ongoing vigilance.
What firewalls can’t do
While a firewall is a security device essential for protecting a computer network, there are limitations to what it can achieve. Different firewalls, such as stateful inspection firewalls, proxy firewalls, and next-generation firewalls, offer various levels of protection, but they cannot address all security concerns.- Firewalls do not stop every kind of attack. They cannot block phishing or social engineering attempts that trick people from the inside.
- Even if you use advanced firewall types, threats from within your own network are still hard to handle.
- A firewall by itself cannot replace an intrusion prevention system, which actively watches for and responds to attacks.
- Firewalls at home or work protect connected devices, but they cannot help if a device is outside that network.
- They also cannot find malware if it is already on a computer.
- While firewalls are important for guarding your network, you still need extra security steps.
The Importance of a Hardware Firewall
Hardware Firewalls, Simplified: Why They Matter and How They Work
Let’s talk about hardware firewalls, those unsung security heroes sitting quietly at the frontlines of your network. Sure, they might not feel as familiar or tangible as your laptop or smartphone, but when it comes to cybersecurity, they’re like the sturdy bouncers protecting your digital nightclub. So, what makes them so effective, and why should you even care? Let’s break it down in a relaxed, conversational way.
A Firewall, but Make It Hardware
First things first—what exactly is a hardware firewall? It’s essentially a dedicated device that blocks or permits network traffic based on rules you (or your IT department) set up.
Unlike software firewalls—which are literally pieces of software running on a computer—a hardware firewall comes with its own operating system that’s built just for one job: protecting your network. It’s like having a personal guard on your doorstep, rather than asking your fridge and your microwave to check IDs at the party.
And here’s the kicker: hardware firewalls don’t just work for one device—they protect everything on your network. PCs, smartphones, IoT devices, servers—you name it.
Powerhouse Performance: Fast and Furious
Let’s get real for a second: nothing kills productivity quite like a slow internet connection. One of the biggest reasons people invest in a hardware firewall is performance. Since it’s a dedicated piece of tech, it doesn’t share resources with apps or processes like a software firewall would.
Translation? No bogging down your device and no sacrificing speed when the network gets busy. Imagine it as an expressway specifically for handling your security traffic, rather than fighting for space on a crowded city street.
For businesses, particularly ones processing high volumes of data (think e-commerce sites or remote working setups), this “speed boost” can be the difference between happy customers and frustrated users clicking away. And who doesn’t want smooth, seamless internet access?
A Fortress You Can Actually Count On
Beyond speed, hardware firewalls are robust—they’re designed to filter huge amounts of data while keeping all the nasties from the internet (like malware or denial-of-service attacks) at bay. Plus, they stay updated independently of your devices.
That’s right! Even if your employees or family members stubbornly skip updating their devices, the hardware firewall’s operating system keeps humming along, applying the latest patches and staying equipped to handle evolving cyber threats.
Think of it like this: if cybercriminals are evolving, constantly inventing new ways to sneak in, isn’t it comforting to know your firewall is adapting just as quickly to keep them out?
Set It and Forget It: Simplified Network Security
Here’s another perk: simplicity. One hardware firewall can protect everything on your network, which means no tedious, individual installations on each device.
- A hardware firewall protects all devices on your network—no need to install security on each one.
- Set the rules once, and every device follows the same security system.
- This is faster and easier than setting up firewalls on each gadget individually.
- IT teams love this central control—it’s simple to update or change rules from one place.
- No need to manage dozens of devices one by one.
For IT teams, this centralization is a game-changer. Need to make adjustments or update policies? It’s all doable from one place, without having to tinker around with dozens of machines. Pretty sweet, right?
Protectli Vault FW4B – 4 Port, Firewall Micro Appliance/Mini PC
The Perimeter Defense You Didn’t Know You Needed
Here’s where hardware firewalls earn their badge of honor: they sit at the edge of your network. This means they evaluate every piece of incoming or outgoing data before it ever touches your devices.
It’s a proactive approach to cybersecurity. Instead of waiting for a virus to get into your system and signal software firewalls to fight back, the hardware firewall stops the malicious traffic in its tracks at the very door.
This is an invaluable feature for businesses handling sensitive data—think hospitals safeguarding health records or e-commerce companies adding an extra buffer to protect customer information during transactions. With a hardware firewall, you’re reducing the risk of breaches or devastating data leaks. And in our hacker-heavy world, that’s priceless peace of mind.

So… Is It Worth the Investment?
That’s the million-dollar question, isn’t it? Is shelling out for a hardware firewall really necessary? The answer depends on what kind of security you need. If you’re running a small home network with basic internet browsing, you might get by with a software firewall bundled into your OS.
But if you’re managing multiple devices, handling sensitive data, or just want a serious upgrade in performance and protection, a hardware firewall isn’t just worth it—it’s indispensable.
Think of it as home insurance. You may not need it every day, but when something goes wrong, you’ll be endlessly grateful you made the investment.
Solid Security, Smarter Management
In short, hardware firewalls are powerhouse devices that don’t just protect your network but elevate its overall performance. From safeguarding against ever-evolving cyber threats to giving you faster speeds and centralized control, they’re a foundational component of a strong security strategy.
And while they might not be flashy—you’re not exactly showing off a firewall at a dinner party, right?—they’re the unsung heroes keeping your digital world safer. So, go ahead. Pat that quiet little box on your network’s perimeter. It’s working hard so you don’t have to.
The Unsung Hero of Your Home Network: Why a Hardware Firewall Matters
In an era where our homes are becoming increasingly connected, the importance of robust cybersecurity measures cannot be overstated. While many are familiar with antivirus software and password protection, there’s an often-overlooked guardian standing watch over our digital domains: the hardware firewall.
This critical component of home networking security deserves a closer look, especially for those who may not be tech-savvy but want to protect their online presence.
What is a Hardware Firewall?

Before diving into its importance, let’s clarify what a hardware firewall is. Unlike software firewalls installed on individual devices, a hardware firewall is a physical device that sits between your home network and the internet. It acts as a gatekeeper, monitoring all incoming and outgoing traffic to protect your entire network from potential threats.
The First Line of Defense
“A hardware firewall is like having a security guard at the entrance of your digital home,” explains Emily Parker, a cybersecurity expert at TechSafe Solutions. “It scrutinizes every piece of data trying to enter or leave your network, ensuring only safe traffic gets through.”
This comprehensive protection is crucial in today’s interconnected world. With the average household now having multiple devices connected to the internet – from smartphones and laptops to smart TVs and thermostats – having a centralized security system is more important than ever.
Advanced Features for Enhanced Security
Modern hardware firewalls come equipped with sophisticated features that go beyond simple traffic filtering. They can detect and prevent various types of cyber attacks, including malware infections and attempts to steal sensitive data.
These devices use advanced algorithms and machine learning to identify potential threats,” Parker adds. “They can recognize patterns in network traffic that might indicate malicious activity, even if it’s a new type of attack that hasn’t been seen before.”
This proactive approach to security is valuable for home users who may not have the expertise to manually configure complex security settings on each of their devices.
Efficiency Without Compromise
One of the key advantages of a hardware firewall is its ability to provide robust security without impacting the performance of your devices. Unlike software firewalls that run on your computer or smartphone and use up system resources, a hardware firewall operates independently.“This means you get top-notch security without slowing down your devices,” notes Augustine Bloom, a network engineer at HomeNet Secure. “It’s especially beneficial for households with multiple devices, as you don’t need to worry about installing and updating firewall software on each one.”The Bottom Line
While many routers come with built-in firewall features, dedicated hardware firewalls offer higher protection and more advanced features. For homes with multiple devices or those handling sensitive information, investing in a hardware firewall can provide peace of mind and a significant boost to network security.As our dependence on connected devices continues to grow, so does the importance of protecting our digital lives. A hardware firewall might not be the most glamorous piece of technology in your home, but it could very well be the most important for keeping your family’s data safe and secure from network address translation vulnerabilities.Protecting Your Family
- Safeguarding Personal Information: Protecting your personal info is crucial in today’s cybercrime world. A hardware firewall stops unauthorized access to sensitive data. This is vital for families, especially with kids who might download risky content.
- Control Over Network Access: A hardware firewall lets you control who can access your network and what they can do. This is great for parents wanting to keep their kids safe online. You can block certain websites or apps, making browsing safer.
How Hardware Firewalls Work
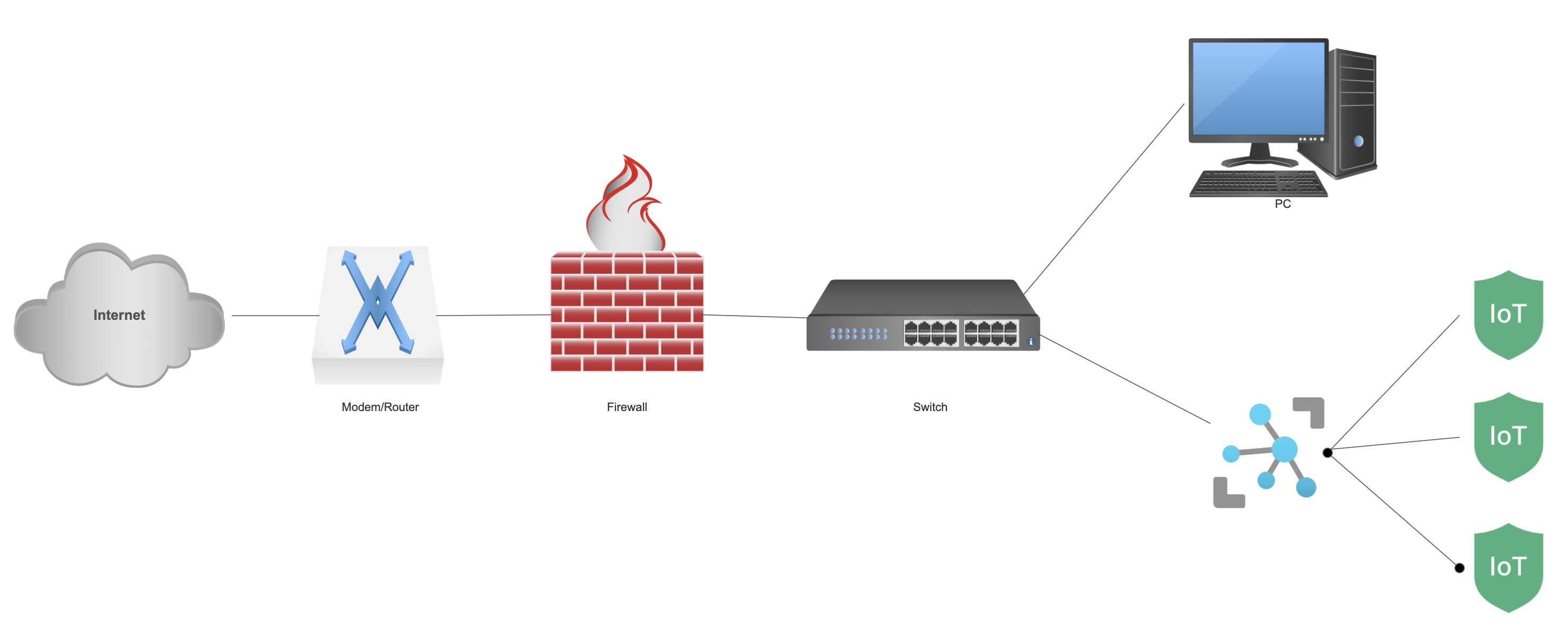
How Does a Hardware Firewall Enhance Security for IoT Devices?
Let’s talk about how hardware firewalls boost security for IoT devices in your home network. These firewalls offer several key advantages. They make protecting smart home gadgets easy.First off, hardware firewalls provide centralized protection. This means all devices on your network, including IoT gadgets, get the same level of security. You don’t need to set up each device separately. It’s a one-and-done solution for your entire network.Another big plus is traffic filtering. The firewall acts as a gatekeeper, blocking malicious content before it reaches your IoT devices. This stops many potential attacks in their tracks. Your smart home stays safer.Hardware firewalls are also great for resource efficiency. Unlike software firewalls, they don’t use up your gadgets’ processing power or memory. This is especially important for IoT devices, which often have limited resources.The firewall’s effectiveness depends on how it’s set up. If it’s not configured right or not updated, it might not protect your network well.Modern hardware firewalls come with advanced features for IoT security. They include intrusion detection and prevention systems to catch suspicious activity. Some can even isolate IoT devices on a separate network for extra security. Plus, they regularly update to patch vulnerabilities and combat new threats, ensuring your firewall security remains strong.Lastly, hardware firewalls offer robust access control. You can set specific rules for your IoT devices. This limits what they can connect to and what kind of traffic they can send or receive. It helps prevent unauthorized access and can limit the damage if a device gets hacked.A hardware firewall acts as a comprehensive security solution for your IoT devices. It provides protection, efficiency, and control in one package.
What are the Main Advantages of Using a Hardware Firewall Over a Software Firewall?
For securing your home network, choosing between hardware and a software firewall can make a big difference. Both have their perks, but let’s dive into why a packet-filtering firewall might just be your best bet.
Centralized protection through a network firewall can simplify management and enhance security across multiple devices.
One of the biggest advantages of a hardware firewall is its ability to protect all the devices on your network with a single defense system. Unlike software firewalls, which need to be installed on each device, a hardware firewall offers a one-stop solution. This means you can easily secure everything from your laptop to your smart fridge, without the hassle of setting up individual protections.
Resource Efficiency
Hardware firewalls are like the unsung heroes of network security—they do their job without hogging your device’s resources. This means your devices stay fast and responsive. On the flip side, software firewalls can slow things down, especially on older gadgets. So, if you’ve got a house full of tech, a hardware firewall is a smart choice.
Advanced Security Features
Modern hardware firewalls come packed with cool features that go beyond basic protection. Think intrusion detection, VPN support for secure remote access, content filtering, and even anti-malware scanning. These features provide a level of security that most software firewalls just can’t match.
Continuous Protection
A hardware firewall is like a vigilant guard that never sleeps. It protects your network 24/7, even when you turn off your devices. This constant protection ensures that your network is always safe from threats.
Simplified Management
Managing your network’s security can be a breeze with a hardware firewall. You can update security rules and monitor activity all from one place, which is perfect if you’re not a tech wizard. It simplifies the process, making it accessible for everyone.
Here is a comparison table outlining the benefits of a software firewall compared to a hardware firewall:
| Feature | Software Firewall Benefits | Hardware Firewall Benefits |
| Cost | Lower initial cost; often includes free trials or affordable subscriptions[1][2]. | Higher upfront cost but no recurring subscription fees; long-term investment[1][2]. |
| Installation | Simple to install and configure; can be deployed remotely on multiple devices[1][2]. | Requires professional installation and physical setup in a network environment[1]. |
| Flexibility | Highly customizable and adaptable to changing security needs; allows fine-grained control[1]. | Less flexible as it relies on pre-configured settings and rules[3]. |
| Portability | Moves with the device (e.g., laptops), providing protection even outside the home network[1]. | Tied to a fixed location; protects only devices within the network[1][4]. |
| Space Requirements | No physical space needed; operates as software on existing devices[1][2]. | Requires physical space, power, and cooling in a controlled environment[1][2]. |
| Traffic Monitoring | Can monitor both inbound and outbound traffic for threats, offering more granular control[1]. | Primarily focuses on inbound traffic; outbound monitoring may require additional configuration[3][4]. |
| Scalability | Scalable for small networks or individual systems without significant performance impact[3]. | Better suited for large networks with high traffic volumes due to dedicated processing power[3][4]. |
| Updates | Easily updated remotely across all devices with minimal effort[1][3]. | Updates require manual intervention or professional assistance in many cases[1][3]. |
| Integration | Works well with other security solutions like antivirus software and cloud-based tools[1][5]. | Provides centralized protection but may have limited integration with third-party tools[5]. |
| Performance Impact | May slow down the host computer as it uses system resources to operate[1][3]. | Operates independently of computer resources, ensuring no impact on device performance[3][4]. |
| Use Cases | Ideal for small businesses, remote workers, and personal devices due to cost and portability[1][2]. | Best for enterprises or organizations requiring robust, centralized protection for large networks[3][4]. |
Summary:
- Software firewalls excel in cost-effectiveness, portability, and customizability, making them ideal for smaller setups or individual users.
- Hardware firewalls provide superior performance, scalability, and centralized protection, making them better suited for larger organizations or high-security environments.
[1] Firewall Types and Selection. Hardware vs Software – zenarmor.com https://www.zenarmor.com/docs/network-security-tutorials/hardware-firewall-vs-software-firewall [2] Hardware vs Software Firewalls: What’s the Difference – FS.com https://www.fs.com/sg/blog/hardware-vs-software-firewalls-whats-the-difference-1980.html [3] What Is A Hardware Firewall? Hardware vs Software Firewalls https://www.fortinet.com/resources/cyberglossary/hardware-firewalls-better-than-software [4] What is the difference between firewall hardware and firewall … https://www.uscybersecurity.net/firewall-hardware-firewall-software/ [5] Hardware Firewalls vs. Software Firewalls – Palo Alto Networks https://www.paloaltonetworks.com/cyberpedia/hardware-firewall-vs-software-firewall [6] hardware vs software firewall : r/homelab – Reddit https://www.reddit.com/r/homelab/comments/wilppc/hardware_vs_software_firewall/ [7] What is a Hardware Firewall? – Check Point Software Technologies https://www.checkpoint.com/cyber-hub/network-security/what-is-firewall/what-is-a-hardware-firewall/
Hardware Firewalls
- Provides enhanced security by filtering network traffic at the physical gateway level
- Operates independently of connected devices, reducing the load on individual systems
- Better suited for businesses with high levels of sensitive data and multiple users
- Offers advanced features, such as intrusion detection and prevention systems (IDS/IPS)
- Can handle large volumes of traffic without impacting network performance
- Less susceptible to being disabled by malware compared to software firewalls
- Reduces the risk of human error in setup and management
- Higher upfront costs compared to software-based firewalls
- May require expert installation and management for optimal performance
- Not ideal for individual or small household users due to complexity
- Ongoing maintenance, such as firmware updates, can be time-consuming
- Limited flexibility for mobile devices when outside the network
- Physical space is needed to house the firewall hardware
Software Firewalls
- Easy to install and configure on individual devices
- Typically more affordable than hardware firewalls
- Provides customizable settings for specific applications and programs
- Can be updated easily to address new security threats
- Ideal for personal use and small-scale security needs
- Works well with mobile devices, offering protection on-the-go
- No additional hardware required, saving physical space
- Consumes system resources, potentially affecting device performance
- Only protects the device it is installed on, requiring installation on multiple devices
- Less effective at handling large-scale traffic for businesses
- Can be disabled by certain types of malware
- Relies on the operating system, potentially making it vulnerable to OS-specific exploits
- May require frequent updates to stay effective against the latest threats
NordVPN is one of the leading Virtual Private Network (VPN) providers, known for its security focus, speed, and vast server network. If you're looking to protect your privacy online, encrypt your internet traffic, bypass geo-restrictions, or secure devices on your home network, NordVPN is a popular choice.
NordVPN really has something for everyone. Privacy enthusiasts love its unique tools, and if you’re just trying to unlock that streaming service you can’t access, NordVPN’s huge selection of servers and location options have you covered. First-time users will find it super easy to get started, and there are plenty of extras to check out too—like encrypted storage and a handy password manager.
- Support for multi-hop, split tunneling, and Tor connections
- Offers strong encryption and security features to ensure privacy
- Large server network with thousands of servers across multiple countries
- No-logs policy ensures user data is not stored or shared
- 24/7 customer support via live chat for troubleshooting
- Monthly subscription cost can be higher compared to some competitors
- No native router app, requiring manual configuration for routers
While both hardware and software firewalls have their place, a hardware firewall offers a more robust, efficient, and user-friendly solution for home network security. Whether you’re protecting a few devices or a whole smart home, the peace of mind a network firewall provides is well worth the investment.
Can Hardware Firewalls be Integrated with Other Security Measures for Enhanced Protection?
Yes, hardware firewalls can work with other security tools for better protection. This approach, called “defense in depth,” boosts your security. Here’s how hardware firewalls and other tools work together:
Intrusion Detection and Prevention Systems (IDS/IPS)
Many hardware firewalls have IDS/IPS. These systems watch for suspicious traffic and block threats. They add an extra layer of security, catching attacks the firewall might miss.
Virtual Private Networks (VPNs)
Hardware firewalls can support VPNs for secure remote access. They encrypt data and ensure only allowed users can get in. The firewall can also enforce VPN policies. Hardware firewalls can manage multiple VPN connections simultaneously, allowing businesses to accommodate many remote users without compromising security.
- Hardware firewalls include intrusion detection and prevention systems (IDPS) to monitor traffic and block threats in real time.
- They allow centralized management, making it easy for IT admins to control VPN settings, update security, and manage user access from one place.
- These firewalls are faster and more reliable than software firewalls because they are built specifically to handle network traffic. This reduces delays and improves performance for tasks like video calls or VoIP.
- They support advanced VPN protocols (e.g., OpenVPN, IPSec, SSL/TLS), giving businesses flexibility to pick the best option for their needs.
- Combining a hardware firewall with VPN features improves remote access security and strengthens the network, keeping data safe while ensuring smooth user connectivity.
Antivirus and Anti-malware Solutions
Firewalls and antivirus software work together to protect against distinct threats. Some firewalls even have antivirus built-in, scanning for malware.
Content Filtering
Hardware firewalls can block harmful websites or limit certain content. This is useful for families wanting to keep their online environment safe for kids.
Network Segmentation
Firewalls can create separate network segments or VLANs. This isolates devices like IoT gadgets from sensitive areas of your network. If one segment gets attacked, the others stay safe.
Security Information and Event Management (SIEM)
For advanced setups, firewalls can work with SIEM systems. SIEM tools collect and analyze log data from security devices, giving a complete view of your network’s security.
Regular Updates and Patch Management
Keeping your firewall updated is key to its effectiveness. Many firewalls can update automatically, protecting against new threats.
Creating a Safe Home for Kids: Childproofing Your Home with Smart Tech
Can a Hardware Firewall be Integrated with a VPN for Added Security?
Yes, combining a hardware firewall with a VPN adds layers of protection to your home network. This setup offers many benefits, including improved firewall security and easier management of network address translation.
Enhanced Encryption
When you add a VPN to a hardware firewall, it ensures all your traffic is encrypted. This makes it hard for hackers to see your data as it moves.
Secure Remote Access
Hardware firewalls support VPNs, allowing you to safely connect to your network from anywhere. This is great for keeping your network safe when you’re not at home.
Traffic Filtering
With a hardware firewall, you can limit VPN traffic to certain ports. This helps block potential attacks. It also checks VPN traffic for suspicious activity, adding more security.
Network Segmentation
Advanced firewalls can create separate networks for VPN traffic. This keeps risky connections away from your main network, adding more security.
Centralized Management
Managing your VPN and firewall together from one place makes things easier. It helps keep your network secure consistently.
Improved Performance
Hardware firewalls handle traffic well, even with VPN encryption. They can manage the extra work without slowing down your network.
Can a Firewall be Bypassed by Skilled Hackers?

Yes, skilled hackers can get past firewalls. They use different methods based on the firewall and network vulnerabilities. But realize, while they CAN bypass a firewall, a firewall is only as strong as its weakest link. This means, if you aren’t keeping up with standard protocols and regular maintenance, you might as well open the door to let them in. That can be prevented simply by staying on top of updates. Here’s how they do it:
Techniques Used to Bypass Firewalls
- Exploiting Misconfigurations
Firewalls work only as well as their setup. If they’re not set up right, they might leave open ports or let in the wrong kind of traffic. This can be a way for hackers to get into the network without permission. - Social Engineering
Hackers often trick people into giving away info or doing things that hurt security. They might send fake emails that look real, tricking people into clicking on bad links. This can get around firewall protections. - Hiding Malicious Payloads
Attackers can hide their bad stuff in files or websites that seem safe. For example, they might put malware in a picture or use trusted sites to send harmful stuff. This way, firewalls that block known threats won’t catch it. - Utilizing Backdoors
Firewalls might have secret ways in which hackers can find. These secret doors let attackers escape security without being caught. It’s important to keep firewalls updated and checked for these backdoors. - Physical Access
If a hacker physically gets into the network, they can easily get past firewalls. They might plug a device into the network or find another way to get around security.
Is it Possible to Detect Firewall Bypassing?
Yes, finding out if someone has bypassed a firewall is possible. But how well you can find it depends on the attack and security you have. Here are some ways to detect it:
Detection Methods
- Advanced Security Tools:
Organizations can employ advanced security measures, such as Endpoint Detection and Response (EDR) tools and intrusion detection systems (IDS). These tools actively monitor network traffic and endpoint activities for suspicious behavior, allowing the detection of malware that may have bypassed the firewall. For instance, if a malicious payload is hidden within a legitimate file, EDR tools can identify unusual patterns or behaviors that indicate a breach. - Anomaly Detection:
By establishing a baseline of normal network behavior, security systems can detect anomalies that may suggest firewall bypassing. For example, if there is a sudden spike in outbound traffic or unusual access to sensitive data, it could show that an attacker successfully bypassed the firewall and is attempting to infiltrate data. - Log Analysis:
Regularly reviewing firewall logs can help identify unauthorized access attempts or unusual traffic patterns. If a firewall is configured to log all traffic, network administrators can analyze these logs to spot suspicious activities that may show an attempt to bypass security measures.
Limitations of Detection
Even though there are ways to detect firewall bypassing, there are challenges:
- Evasion Techniques
Skilled hackers use tricks to avoid being caught. They might encrypt their traffic or use sneaky methods to not trigger alerts. This makes it hard for security to find the bad stuff. - Misconfigurations
If a firewall isn’t set up right, it might not log or alert on certain traffic. This lets attackers work without being noticed. It’s important to regularly check and update firewalls to keep them working well.
Is Continuous Monitoring Necessary to Detect Bypassing?
Continuous monitoring is not just important; it is absolutely vital for the robust detection of firewall bypassing. While you don’t need to be glued to your system round the clock, staying vigilant is crucial. Regularly checking for firmware updates can make all the difference in ensuring your defenses remain effective against evolving threats.
Many of these updates occur automatically, yet a proactive approach will empower you to safeguard your network more effectively. Don’t leave your security to chance—commit to regular monitoring today and fortify your defenses against potential vulnerabilities!
Here’s why it plays a crucial role in maintaining network security:
Real-Time Monitoring
Continuous monitoring allows organizations to observe network traffic in real-time. This capability is vital for identifying suspicious activities that may indicate an attempt to bypass firewall protections.
By capturing data such as source and destination IP addresses, ports, and protocols, security teams can quickly spot anomalies that could signify a breach or an evasion attempt.
Vulnerability Identification
Regular monitoring helps uncover potential weaknesses in firewall configurations or performance. By continuously assessing the effectiveness of the firewall, organizations can identify and rectify vulnerabilities before attackers can exploit them. This proactive approach is crucial in a landscape where cyber threats are constantly evolving.
Response to Evolving Threats
Adaptability
Cybercriminals frequently change their tactics to bypass security measures. Continuous monitoring enables organizations to adapt their defenses to new threats. For instance, if a particular method of bypassing is detected, security teams can adjust firewall rules or implement additional security measures to counteract that specific threat.
Audit and Compliance
Continuous monitoring is not just about detecting threats, but also involves ensuring compliance with security policies and regulations. Regular audits of firewall logs and configurations can help maintain alignment with organizational security standards, ensuring that any unauthorized changes or vulnerabilities are promptly addressed.
Can Firewall Rules Prevent Bypassing Attempts?
Yes, properly configured firewall rules can significantly help prevent bypassing attempts, although they are not foolproof. Here’s how firewall rules contribute to preventing bypassing:
Traffic Filtering
Firewall rules define what types of traffic are allowed or blocked. By setting strict rules, you can filter out potentially malicious traffic before it enters your network. For example, you can block traffic from known malicious IP addresses or restrict access to certain ports commonly exploited by attackers.
Access Control
Firewall rules can be used to control who has access to your network and what resources they can reach. By implementing the principle of least privilege, you can ensure that users and devices only have access to the resources they need, reducing the potential attack surface.
Application-Level Filtering
Advanced firewalls can implement rules based on application-level data to enhance firewall security. This allows for more granular control, such as blocking specific types of file transfers or restricting access to certain web applications.
Stateful Inspection
Many modern firewalls use stateful inspection, which keeps track of the state of network connections. This allows the firewall to make more informed decisions about whether to allow or block traffic based on the context of the connection.
Logging and Alerting
Firewall rules can be set to log suspicious activities and generate alerts. While this doesn’t directly prevent bypassing attempts, it allows quick detection and response to potential threats.
Limitations of Firewall Rules
While firewall rules are crucial for security, they have limitations. While firewall rules are crucial for security, they have limitations: they may not adapt effectively to evolving threats, as attackers often develop new techniques that can bypass established rules. Moreover, a focus solely on network traffic can lead to a false sense of security, as vulnerabilities within applications or user behaviors remain unaddressed.
Firewalls might also struggle with encrypted traffic, making it difficult to inspect for malicious content. Additionally, misconfigurations can create gaps in security, exposing systems to attacks that might have been otherwise mitigated.
Effective security requires a multi-layered approach, integrating firewalls with other protective measures such as intrusion detection systems, regular software updates, and user education to create a more robust defense against the ever-changing landscape of cyber threats.
- Zero-Day Exploits: Firewall rules may not protect against new, unknown threats.
- Insider Threats: Rules typically focus on external threats and may not prevent attacks within the network.
- Complexity: As networks grow more complex, managing firewall rules becomes more challenging, potentially leading to misconfigurations.
- Encrypted Traffic: Some firewalls may have difficulty inspecting encrypted traffic, attackers.
Best practices for configuring a hardware firewall
Here are some best practices for configuring a hardware firewall to maximize security for your home network:
- Change default passwords and usernames
Don’t keep the default admin credentials that come with the firewall. Create strong, unique passwords. - Keep firmware updated to maintain the effectiveness of your network firewall.
Regularly check for and install firmware updates from the manufacturer to patch vulnerabilities. - Enable logging
Turn on logging features to track traffic and potential threats. Review logs periodically. - Use the principle of least privilege to ensure that your security software only grants access to necessary resources.
Only open ports and allow traffic that is absolutely necessary. Block everything else by default. - Implement egress filtering
Control outbound traffic in addition to inbound to prevent malware from communicating out. - Enable intrusion prevention features
Turn on IPS capabilities to detect and block known attack patterns. - Segment your network
Use VLANs or multiple interfaces to separate devices and limit lateral movement. - Configure remote access securely
If enabling remote management, use strong authentication and encryption. - Disable unnecessary services
Turn off any services or protocols you don’t actively use. - Use application-layer filtering
Enable deep packet inspection to filter traffic based on applications, not just ports. - Test your configuration
Regularly scan your network and test the firewall to ensure rules are working as intended. - Document your setup
Keep detailed records of your firewall configuration for troubleshooting and auditing.
The key is to take a “default deny” approach and only allow the minimum required for your network to function. Regularly review and update your rules as needs change. While no configuration is perfect, following these best practices will significantly improve your network security.
Final Thoughts
Firewall rules are a great way to block bypass attempts, but they work best when they’re part of a bigger security plan. To keep your network safe, pair well-configured firewall rules with regular updates, continuous monitoring, and a layered defense strategy. While no single solution can completely block attackers, solid firewall rules make it much harder for them to break in.
Want to strengthen your defenses even more? Adding intrusion detection and prevention systems (IDPS) is a smart move. These tools keep an eye on traffic, watch for anything suspicious, and respond to threats in real time. Just make sure they’re set up properly—too many false positives can be a headache, and false negatives could leave gaps in your defenses.
It’s also important to regularly check your network’s security. Security audits and vulnerability assessments help you find and fix weak spots before attackers can exploit them. Combine that with employee training on cybersecurity best practices, and you’ll build a team that’s more aware and prepared to handle threats.
Another great strategy is adopting a zero-trust framework. This means verifying every user and device that tries to access your network—no exceptions. By sticking to least privilege access, you can limit permissions to exactly what each person or device needs, reducing the risk of unauthorized access or mistakes.
At the end of the day, firewall rules are just one piece of the puzzle. Keeping your network and digital assets safe takes a smart, adaptable security strategy. With the right tools, regular updates, and a focus on staying ahead of new threats, you’ll be in a much stronger position to protect what matters most.
Features
| Processor | 1.6 GHz celeron |
| RAM | 8 GB DDR3L |
| Hard Drive | 120 GB SSD |
| Chipset Brand | Intel |
| Card Description | Dedicated |
| Brand | Protectli |
| Series | FW4B – 4 Port |
| Item model number | FW4B-0-8-120 |
| Hardware Platform | PC |
| Operating System | Windows |
| Item Weight | 3.52 pounds |
| Product Dimensions | 4.5 x 4.3 x 1.5 inches |
| Item Dimensions LxWxH | 4.5 x 4.3 x 1.5 inches |
| Color | Black |
| Processor Brand | Intel |
| Number of Processors | 1 |
| Computer Memory Type | DDR3 SDRAM |
| Flash Memory Size | 120 |
| Hard Drive Interface | Solid State |
| Batteries | 1 CR2 batteries required. |
- THE VAULT (FW4B): Secure your network with a compact, fanless & silent firewall. Comes with US-based Support & 30-day money back guarantee!
- CPU: Intel Quad Core Celeron J3160, 64 bit, up to 2.2GHz, AES-NI hardware support
- PORTS: 4x Intel Gigabit Ethernet ports, 2x USB 3.0, 1x RJ-45 COM, 2x HDMI
- COMPONENTS: 8GB DDR3L RAM, 120GB mSATA SSD. coreboot BIOS optional, must be installed by user.
- COMPATIBILITY: No OS pre-installed. All hardware tested with pfSense, untangle, OPNsense and other popular open-source software solutions.
FREQUENTLY ASKED QUESTIONS
What is a firewall, and why do I need one for my home network?
A firewall is a security system that monitors and controls incoming and outgoing network traffic based on predefined rules. For home networks, it helps block unauthorized access, protect personal information, and prevent cyberattacks.
What are the differences between hardware and software firewalls?
Hardware firewalls are physical devices that sit between your router and the internet to filter traffic, while software firewalls are applications installed on individual devices. Both protect your network, but hardware firewalls cover all devices, whereas software firewalls focus on specific systems.
Can a firewall protect against all types of cyber threats?
No, a firewall is an essential layer of defense but won’t catch every threat. It’s most effective when paired with other security measures like antivirus software, intrusion detection systems, and strong passwords.
How do I set up a firewall for my home network?
Most modern routers have a built-in firewall that’s easy to activate through the router’s settings. For additional protection, you can also install third-party firewalls or use dedicated hardware devices.
Does a firewall slow down my internet connection?
A properly configured firewall should have minimal impact on your internet speed. However, older or low-quality devices may cause slight delays when filtering traffic.
What settings should I configure on my home firewall?
Common settings include enabling intrusion protection, blocking suspicious ports, and setting up access control to allow or deny connections based on specific criteria. Many firewalls also have pre-configured options to simplify setup.
What is the difference between a firewall and a VPN?
A firewall protects your network from outside threats by blocking unauthorized traffic, while a VPN (Virtual Private Network) encrypts your internet connection to protect data privacy during online activities. They serve different purposes but work well together.
Do I need a firewall if I have antivirus software?
Yes, antivirus software protects your devices from malware, while a firewall prevents unauthorized access to your network. Both are important for comprehensive home network security.
Can I monitor traffic on my home network using my firewall?
Many firewalls, particularly modern hardware or software solutions, allow you to monitor your network traffic in real-time and identify unusual activity or potential threats.
What should I do if my firewall blocks legitimate traffic?
If your firewall is blocking useful or legitimate traffic, you can adjust its rules or create an exception for that specific traffic or application. Refer to your firewall’s documentation for guidance on creating custom rules.
“`Bringing 25+ years of expertise in graphic design, marketing, and advertising to Nerdy Home Tech. Specializing in demystifying home automation and AI, I craft engaging content that simplifies complex tech for newbies and seasoned pros alike. Join me on a journey through the world of smart home tech!