Is Your Smart Home Listening In? The Shocking Reality Behind Our Convenient Gadgets
Imagine you’re enjoying a cozy night in and suddenly think your smart speaker is listening to your conversation. With the rise of smart home devices, there are growing worries about privacy breaches. This post will discuss what data these devices collect, how they do it, and weigh the risks and benefits of a connected home.
What Information Do Smart Home Devices Collect?
Smart home devices can collect a wide range of data, including:
- Voice recordings: Smart speakers and voice assistants like Amazon Alexa and Google Home are always listening for their wake words, and may inadvertently record private conversations.
- Video footage: Security cameras and smart doorbells can capture video of your home and anyone who enters or leaves.
- Usage data: Smart appliances, thermostats, and other devices can track your habits and preferences, such as when you’re home, your energy usage, and even your grocery list.
- Location data: Some smart speakers have built-in GPS, allowing them to track your location within your home.
How Do Smart Home Devices Collect This Information?
Most smart home devices rely on built-in microphones and cameras to gather data. Voice recognition technology allows devices to respond to user commands, but also means they are constantly listening. Smart devices also communicate with external servers through the Internet of Things (IoT), potentially sharing user information, making data security paramount. Some devices have motion sensors or use facial recognition to gather data, integrating these features with privacy-enhancing technology.
Smart home devices have become highly sophisticated, incorporating various technologies to improve user experience and convenience. However, this complexity also raises several important considerations related to privacy and data security. Let’s break this down further:
Microphones and Cameras:
- Voice Recognition: Microphones in devices like smart speakers (e.g., Amazon Echo, Google Home) and smart assistants (e.g., Siri, Alexa) are always in a state of listening for a wake word. This functionality means these devices can start recording and processing commands, which raises privacy concerns about unintended recording of private conversations.
- Cameras: Smart cameras and doorbells (e.g., Ring, Nest Cam) often feature live streaming and recording capabilities. Some can even recognize faces to differentiate between known individuals and strangers. While useful for security, these features can lead to concerns about unauthorized access or data breaches, resulting in surveillance footage being leaked.
Internet of Things (IoT):
- Communication: Smart devices often communicate with each other and external servers over the Internet. This connectivity allows seamless operation and enhanced functionality. However, it also means that data, including potentially sensitive information, is transmitted over networks, sometimes to third-party servers.
- Integration: Many smart home devices integrate, creating a web of interconnected devices. If one device’s security is compromised, it might provide a gateway to other devices in the network.
Data Sharing and Security:
- Data Encryption: To protect user information, data encryption both in transit and at rest is essential. Ensuring all communication between devices and servers is encrypted minimizes the risk of data interception.
- User Control: Giving users clear control over what data is collected and used, including the ability to delete recordings and other personal information, is critical for maintaining trust.
- Regular Updates and Patching: Manufacturers need regular software updates to address newly discovered vulnerabilities. Users should ensure their devices always run the latest firmware to protect against security threats.
Motion and Facial Recognition:
- Motion Sensors: Devices like smart lights and security systems often use motion sensors to detect activity and trigger actions. While less invasive, these sensors can still gather and transmit data about user movements, creating a potential vector for privacy concerns.
- Facial Recognition: This technology can be powerful, but brings significant privacy considerations. Storing facial recognition data securely and using it ethically is of utmost importance, as misuse can have severe privacy implications.

The Role of Cookies in Consumer Retargeting
Smart home devices might be all the rage, but let’s talk about something a little less flashy—cookies on your web browser. These tiny data files are stored on your device whenever you visit a website, keeping track of things like your browsing habits, preferences, and even your shopping history. They’re a goldmine for companies wanting to tailor ads just for you.
Ever been window-shopping online for a new laptop, only to find yourself bombarded with ads for laptops and accessories everywhere you go? That’s cookies at work. By analyzing the info they collect, companies can retarget you with ads that match your interests, making it harder to resist clicking “add to cart.”
Essential Guide to Firewalls for Home Networks and Small Offices
The primary danger posed by these cookies lies in the depth and breadth of personal data they can amass over time. This relentless tracking can lead to an erosion of privacy, as detailed profiles about users’ internet habits, preferences, and even personal interests are created and potentially shared or sold to third parties without explicit consent.
This not only raises privacy concerns but also security risks if this data falls into the wrong hands through data breaches, compromising data security.
To mitigate these risks and protect your browsing history, consider taking the following steps to enhance data security, privacy-preserving protocols, and authentication processes:
- Use Incognito or Private Browsing Modes: These modes prevent the storage of cookies, search history, and other data on your device.
- Adjust Your Browser’s Privacy Settings: Most browsers allow you to limit or block cookies. Adjust these settings to suit your privacy preferences.
- Use Privacy-Focused Browsers: Browsers like Brave or Firefox Focus are designed to automatically block trackers and cookies, enhancing your online privacy through privacy-preserving technologies.
- Install Ad Blockers and Tracking Protection Tools: These can help prevent trackers from following your online activity.
- Regularly Clear Cookies to maintain data sovereignty: Make it a habit to regularly clear the cookies from your browser to remove any accumulated data that could be used for tracking.
By adopting these measures, you can significantly reduce the likelihood of cookies tracking your online behavior, thus enhancing your digital privacy and security.

How is This Data Used?
Companies that manufacture smart home devices may use the collected data for various purposes, such as:- Personalization and targeted advertising: By analyzing your usage patterns and preferences, companies can tailor their products and services to your interests, and even use the data for targeted advertising. Personalization and targeted advertising have become increasingly prevalent as companies strive to better meet the needs and preferences of their customers. By leveraging data analytics and artificial intelligence, companies can gain insights into individual habits, preferences, and behaviors.
- Product improvement and development: Manufacturers may use the data to identify areas for improvement and develop new features for their devices.
- Selling anonymized data sets to third parties: Some companies may sell aggregated, anonymized user data to third parties for market research or other purposes.
Hidden Costs of Convenience: How Free Social Media Pays With Your Privacy
In today’s world, where convenience and connectivity often come first, it’s easy to forget that nothing online is truly free. Social media platforms are a perfect example. They may not charge you a dime, but they’re not really “free.” Ever heard the saying, “If you’re not paying for the product, you are the product”? It’s true—and it’s something we should all take seriously.- Companies collect a lot of personal data, including your age, gender, interests, friends, and even your location.
- Every action—likes, shares, comments, and even how long you look at a post—is tracked.
- They claim it’s to improve your experience, but the real goal is to sell your data to advertisers for targeted ads. Essentially, your information becomes their product.
Why This Matters:
Privacy Concerns:
- Most people don’t realize how much data they’re sharing because the terms of service are confusing and lack transparency.
- This creates a serious breach of privacy.
Data as a Commodity:
- Companies analyze and sell your online behavior, turning every action into profit.
- Constant tracking increases the risk of your data being misused or falling into the wrong hands.
Real-World Impact:
- Data has been used to manipulate opinions, influence elections, and even commit crimes like identity theft and cyberstalking.
Surveillance Economy:
- We’ve entered a system where privacy is traded for convenience and connectivity.
- This trend puts users at risk while benefiting companies financially.
What You Can Do:
- Use tools like anonymization technologies to protect your privacy.
- Be mindful of how much personal information you share online.
- Consider whether the convenience of “free” services is worth the cost to your privacy.
Protecting your home network is crucial. Do it with the help of a firewall like, Firewalla: Cyber Security Firewall
The Privacy Risks of Smart Home Devices
While smart home devices offer convenience and enhanced functionality, they also pose significant privacy risks, including:- Security concerns: Smart devices are vulnerable to hacking and data breaches, which could cause sensitive information falling into the wrong hands.
- Invasion of privacy: With the constant monitoring and recording capabilities of smart devices, there is a risk of personal conversations and activities being exposed without consent.
- Data misuse: Companies may use gathered data for purposes beyond what users originally agreed to, such as selling it to third parties or using it for targeted advertising.
The Benefits of Living in a Connected Home
Despite the privacy concerns, there are also benefits to living in a connected home, including enhanced automation and convenience.- Convenience and efficiency: Smart devices can automate tasks and make daily life more convenient by adjusting lights, temperature, and other settings according to your preferences.
- Accessibility: Smart technology can assist individuals with disabilities or limited mobility, making tasks like turning on lights or adjusting the thermostat easier.
- Energy savings: With smart thermostats and energy monitoring devices, homeowners can reduce their energy usage and save money on utility bills.
Protecting Your Privacy in a Smart Home
Always prioritize your privacy and take necessary precautions when using connected devices.
Although it may be impractical to fully eradicate privacy risks linked to smart home devices, you can mitigate the risks by taking certain measures, such as:
- Investigate before purchasing: Prior to buying a smart home device, look into the company’s privacy policies and data collection practices.
- Deactivate unnecessary features: If certain features on your smart devices aren’t needed, turn them off to reduce the amount of data gathered.
- Stay updated and maintain your devices: Stay informed about security and privacy concerns related to your smart devices, and consistently update their software to ensure they have the latest security fixes.
Leveraging a Virtual Private Network (VPN)
Leveraging a Virtual Private Network (VPN) like the one I use, NordVPN, at home is an excellent strategy to enhance your smart home’s security posture. A VPN serves as a secure tunnel between your device and the internet, encrypting data traffic to protect your online identity from potential eavesdroppers.
This encryption prevents hackers and other unwanted snoopers from intercepting your internet traffic, maintaining the confidentiality and integrity of your personal information.
The benefits of using a VPN in a smart home environment extend beyond privacy protection. It also allows you to circumvent geographic restrictions by masking your actual IP address, offering you the freedom to access international content that may not be available in your region, enhancing your data’s sovereignty.
A VPN can significantly reduce the risk of cyber attacks directed at your smart home devices, by hiding their presence from the public internet, making them less likely to be targeted by automated scanning tools used by attackers.
Here are some additional tips that can further secure your smart home along with the use of a VPN:
- Always make sure your VPN is active, especially when conducting sensitive transactions or operating your smart home devices remotely.
- Choose a reputable VPN service provider that follows a strict no-logs policy and offers robust encryption standards. We choose NordVPN.
- Connect all your smart home devices through a dedicated VPN router to ensure comprehensive protection throughout your home network.
By integrating a VPN into your smart home’s security strategy and enjoy the added benefits of unrestricted internet access.
Finally, don’t forget to regularly review your home network’s security measures, such as firewalls and antivirus software. These can help protect not only your smart home devices but also all of the other devices connected to your network.
With these additional tips, you can further enhance the privacy and security of your smart home. Remember to always prioritize your privacy and stay informed about the latest developments in smart home technology.
Don’t forget to regularly check and update your VPN software to get the latest security features and protection. A VPN can significantly boost your privacy in a smart home, but remember to also use strong passwords, ensure your firmware is up-to-date, and be careful with suspicious links or downloads. With the right steps and a VPN, you can enjoy your smart home’s benefits without giving up your privacy.
Smart Home Security Best Practices
 The rapid evolution of smart home technology has brought convenience and efficiency to our daily lives. However, with this digital revolution comes a significant responsibility: the need to secure our interconnected devices. As smart homes become more common, it is our responsibility to prioritize the security of these systems to protect against unauthorized access and data breaches.
The rapid evolution of smart home technology has brought convenience and efficiency to our daily lives. However, with this digital revolution comes a significant responsibility: the need to secure our interconnected devices. As smart homes become more common, it is our responsibility to prioritize the security of these systems to protect against unauthorized access and data breaches.
There are several steps that homeowners can take to ensure the security of their smart homes. Foremost, it’s VERY important to update all devices and software regularly to ensure they have the latest security patches. This can help protect against known vulnerabilities that cybercriminals may exploit.
It is essential to use strong, unique passwords for each device and to change them regularly. Avoid using default passwords or easily guessable passwords, as these can make your devices more vulnerable to attack. Another important security measure is to secure your home network with a strong password and enable encryption such as WPA3. This can help prevent unauthorized individuals from accessing your network and connected devices.
It is also a recommendation to segment your network by creating separate networks for your smart devices, computers, and other connected gadgets. This can help protect your most sensitive data and devices from potential threats. Lastly, consider investing in a reputable cybersecurity solution specifically designed for smart home devices. These tools can help detect and mitigate potential threats, providing an extra layer of protection for your digital ecosystem.
By taking these proactive measures, homeowners can enjoy the convenience and benefits of smart home technology while also safeguarding their security and privacy. As the internet of things continues to grow, prioritizing cybersecurity is crucial to protect our homes and sensitive information from cyber threats.
Why Regular Updates are Crucial for Smart Home Devices
Regularly updating your smart home devices and their accompanying apps is essential to security. These updates often contain patches for security vulnerabilities that, if exploited, could allow hackers to gain control of your devices or access your personal information. Ensuring all devices are running on the latest software version can significantly reduce the risk of a security breach.
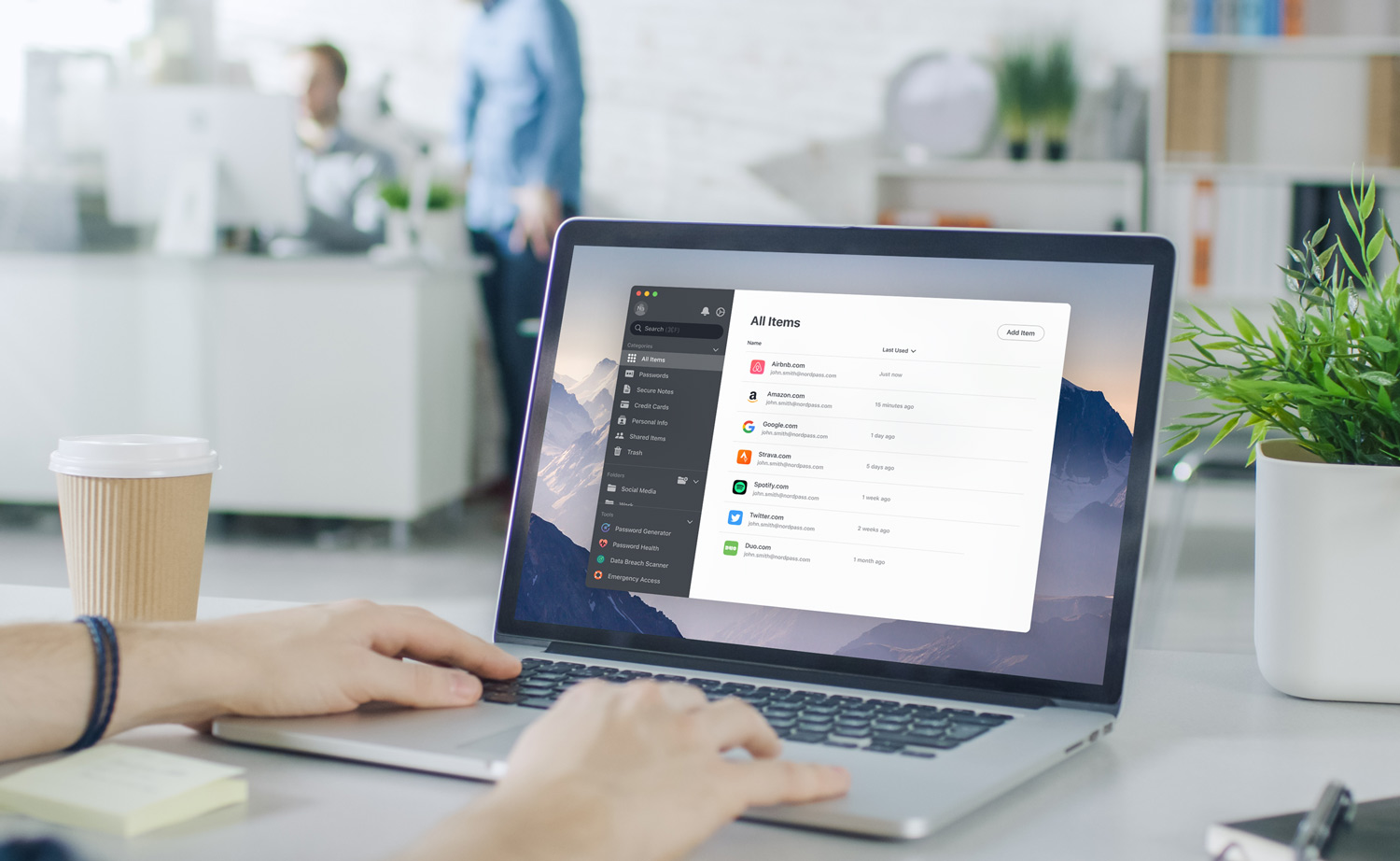
NordPass Password Manager Review: Secure Your Digital Life in 2025
Steps to Update Your Smart Home Devices and Apps
- Check Device Manufacturer’s Website: Regularly visit the website of your smart device manufacturers to check for new updates.
- Enable Automatic Updates: Where possible, enable settings that allow your devices to automatically download and install updates.
- Verify UpdatesAfter updating, verify that the installation was successful and that your device is running the latest version for optimal security and portability, ensuring privacy-preserving protocols are in place.
The Importance of Strong and Unique Passwords
Strong and unique passwords are your first line of defense against cyber intruders. Each device in your smart home network should have a unique password that is complex and difficult to guess, combining letters, numbers, and special characters.
Tips for Creating and Managing Strong Passwords
- Use a Password Manager to bolster data security and simplify the automation of unique, strong passwords across different accounts.: To keep track of multiple strong passwords, consider using a password manager.
- Avoid Common Passwords: Steer clear of easily guessable passwords such as “123456” or “password”.
- Change Passwords Regularly: Update your passwords periodically to further enhance security and ensure hackproof systems.
What Data Your Smart Devices Collect
Smart devices can collect a wide range of data from usage patterns to voice commands, which can be stored in the cloud for further analysis. Understanding what data is collected and how it is used is crucial for maintaining your privacy.
How to Limit Personal Information Exposure
- Customize Privacy Settings: Adjust the privacy settings on each device to minimize data sharing.
- Review Terms of Service to understand the implications for your data privacy and safety.: Understand the terms of service for each device to see how your data may be used or shared, focusing on methods that ensure privacy.
Navigating Privacy Settings on Smart Devices
Learning to navigate and adjust the privacy settings on your smart devices is a key step in safeguarding your personal information.
Best Practices for Privacy Settings Adjustments
- Regular Reviews: Periodically review the privacy settings on each device.
- Restrict Data SharingLimit the amount of data shared with device manufacturers and third-party apps to ensure maximum safety and transparency.
Risks of Third-Party Devices and Apps
Integrating third-party devices into your smart home system can introduce security vulnerabilities if proper authentication and data security measures are not in place. It’s important to assess the security standards of these third-party products before integration, ensuring they include lock and privacy-enhancing features.
How to Safely Integrate Third-Party Solutions
- Research Before Buying: Investigate the security measures and reputation of the third-party device or app.
- Regular Security Assessments: Continually evaluate the security posture of third-party integrations.
Advantages of Using VPNs for Smart Homes
A Virtual Private Network (VPN) can provide an additional layer of security by encrypting your internet connection and shielding your smart home devices from unwanted scrutiny.
Guide to Choosing and Setting Up a VPN
- Select a Reputable VPN Provider: Choose a VPN known for strong security measures.
- Configure VPN on Your Router: Set up the VPN directly on your router to protect all connected devices.
Keeping Up with Security Breaches and Vulnerabilities
Staying informed about the latest security breaches and vulnerabilities affecting smart home technologies can help you react swiftly and protect your network.
Steps to Take After a Security Breach
- Immediate Update: Quickly apply any necessary patches or updates to maintain the device’s hackproof status.
- Change Passwords: Change all passwords related to compromised devices.
Smart Home Security Educational Resources for Families
Educating yourself and your family on smart home privacy and security is vital. Numerous online resources, webinars, and workshops are available to help families stay safe and adhere to data security best practices, often incorporating privacy-enhancing techniques.
Workshops and Training on Smart Home Privacy
- Local Community Centers: Often offer free or low-cost cybersecurity workshops.
- Online Platforms are encouraged to use privacy-enhancing methods.: Provide webinars and courses tailored to smart home security.
Importance of Regular Data Backup
Backing up the data from your smart home devices ensures that you can restore your system to its previous state in the event of a cyber attack or system failure, maintaining data safety.
How to Effectively Backup Smart Home Data
- Automated Backup Solutions: Utilize automated systems to regularly backup your data without manual intervention, incorporating privacy-enhancing methods.
- Secure Storage: Use secure, encrypted storage solutions to protect your backups and ensure compliance with GDPR.
Identifying and Disabling Unnecessary Device Features
Many smart home devices come equipped with features that may not be necessary and can pose security risks if enabled.
Benefits of Minimalist Approach to Smart Device Usage
- Reduced Attack Surface enhances data security.: Fewer active features mean fewer potential vulnerabilities, thereby increasing data security.
- Enhanced Performance: Devices often perform better with fewer active functions.
Tools and Techniques to Monitor Suspicious Activities
Monitoring your smart home for any unusual or suspicious activity is crucial for early detection of potential security threats and ensuring safety.
What to Do in Case of Suspicious Findings
- Immediate Isolation: Disconnect potentially compromised devices from your network.
- Consult Professionals: Seek assistance from cybersecurity professionals to assess and mitigate any damage.
Privacy Laws Relevant to Smart Home Users
Understanding the privacy laws that apply to smart home technology can help you make informed decisions about device setup and data management.
How to Ensure Compliance with Local Regulations
- Legal Consultation: Consider consulting with a legal expert in technology and privacy laws to ensure compliance.
- Regular Updates: Keep your policies and device settings updated in accordance with new regulations.
Benefits of Network Segmentation in Smart Homes
Creating separate networks for your personal and smart home devices can greatly enhance your overall network security, ensuring safety and privacy-preserving practices.
Step-by-Step Guide to Segregate Your Networks
- Dedicated IoT Network: Set up a separate Wi-Fi network exclusively for your smart devices.
- Strict Access Controls: Implement strong access controls and monitoring on your primary network.
How to Change Default Settings for Better Security
Changing the default settings, especially default passwords, on new smart home devices is a critical step in securing your smart environment.
Examples of Default Settings That Should Be Changed
- Default Passwords: Always change default passwords to a strong, unique alternative.
- Default Network Settings: Modify default network settings to limit external access and ensure remote access features are securely configured for end-to-end security.
The Risk of Personal Information Exposure
Sharing personal information through your smart home devices can expose you to risks such as identity theft and unauthorized surveillance.
How to Protect Personal Information in Smart Homes
- Use Encrypted Communication: Ensure that all communications between your devices are encrypted.
- Control Device Permissions: Be selective about which devices have access to sensitive information.
Assessing and Enhancing Your Home Network Security
Your home network is the backbone of your smart home security. Ensuring it is secure against external threats is essential.
Firewalls and Antivirus: Essentials for Smart Homes
- Implement Firewalls to enhance network safety and intrusion prevention.: Use firewalls to protect your network from unauthorized access.
- Use Antivirus Software: Install antivirus software on all devices that connect to your home network to prevent malware infections.
Protectli FW4B Review: Strengthen Your Home Network Security
Final Thoughts on Security and Privacy

This comprehensive guide not only provides you with the knowledge to protect your smart home but also empowers you to implement practical solutions to enhance your privacy and security. Stay vigilant and proactive in managing the security of your smart home environment to enjoy the full benefits of this innovative technology while maintaining high safety standards.
Smart home devices are handy and offer lots of benefits, but they also come with privacy concerns. It’s important to know how these devices use your data so you can make smart choices and keep your privacy safe. Finding a balance between enjoying the benefits and understanding the privacy risks is key. By doing your homework, keeping up with updates, and being careful with your data, you can get the most out of your smart home without giving up your privacy. Employ privacy-enhancing methods to further secure your information. Taking steps like updating your devices regularly, using strong passwords, and choosing privacy-focused options can help keep your personal info safe, allowing you to safely enjoy the benefits of smart technology.
Protecting your home network is crucial. Do it with the help of a firewall like, Firewalla: Cyber Security Firewall
Features
| Product Dimensions | 3.6 x 2.36 x 1.18 inches |
| Item Weight | 10.8 ounces |
| ASIN | B0BYMN4YZ3 |
| Date First Available | March 16, 2023 |
| Manufacturer | Firewalla LLC |
- COMPATIBILITY: This is * Firewalla Purple SE*. The IPS functionality is limited to 500 Mbits. This device can be a router or bridging your existing router. When in simple mode, this device may not be compatible with all routers. Please look at the “specification sheet” document in this listing, or compatibility guide in the manufacturing site for routers that works with Firewalla. May require login to your router and to do basic configuration.
- COMPLETE CYBERSECURITY PROTECTION – Firewalla’s unique intrusion prevention system (IDS and IPS) protects all of your home wire and wireless internet of things devices from threats like viruses, malware, hacking, phishing, and unwanted data theft when you’re using public WiFi. It’s the simple and affordable solution for families, professionals and businesses. Let Firewalla’s built-in OpenVPN server keeps your device usage as secure as it is in your home.
- PARENTAL CONTROL AND FAMILY PROTECT – The days of pulling the power cord from the dusty old router are behind you; with just a few taps on the smartphone, you can see what they’re doing, cut off all access, or cut off only gaming or social networks. Turn on Family Protect to filter and block adult and malicious content, keep internet activities healthy and safe.
- ROUTER MODE – Use the Purple SE as your main router for advanced features including: policy based routing to forward traffic anyway you want, smart queue to decongest your network and prioritize important network traffic, or network health monitoring, all of which give you control over your network and ensure that your network is performing at the optimal capacity and quality.
- DEEP INSIGHT – Firewalla uses deep insight and cloud-based behavior analytics engines to actively detect and automatically block problems as they arise. From this continuous monitoring, you’ll have full visibility of activities across all your iot devices and the ability to identify full network flows, bandwidth analysis, and internet troubleshooting. Keeping your internet secure, and hack free.